Why would you want a “black phone”, one that’s not susceptible to the privacy holes found in all of today’s smartphones? That’s a question that Jaime Rivera touched on at this year’s MWC. The answer is fairly simple, given today’s circumstances and situations. But let’s jump back a few years before we get to that.
Looking back even three or four years, if someone had told you that various companies and law enforcement agencies could track where you were down to a few dozen feet, and were actually doing so (and without a warrant, no less), you’d probably have thought that person was a bit off.
If they’d told you that those same companies and “security agencies” were monitoring your emails, and that they didn’t need a warrant to do that either, you’d probably think that person was border-line “crazy”.
Then, had that person told you that the NSA and other government agencies (in cooperation with foreign government agencies) were collecting information on virtually every single phone call made and text message sent that started or ended in these United States, you’d probably start looking for that person’s tin-foil hat.
Finally, to top it all off, had that person told you that your Internet traffic was being intercepted and monitored, and the basic SSL encryption could be broken in a relatively short amount of time, you’d probably be waiting for the punchline — only it wasn’t a joke.
Fast forward to today: it’s all true, and you owe that guy an apology.
Yes, folks. The people you once considered “crazy nut jobs” were entirely right. If they were right about all that, what about all their other “crazy” claims? Might those be correct, too? Makes you think about things a little differently, doesn’t it?
Encryption isn’t just for securing purchases any longer. Now, encryption is needed for every bit of communication and data that comes to or leaves our devices. Unfortunately, none of the major players offers it — they can’t.
With all the major OSes, manufacturers, and carriers, you’re running naked through streets — figuratively speaking. What’s worse, all these companies are subject to quasi-legal orders to “share” their information with various agencies, which usually come with gag orders attached, prohibiting them from even making mention of what they’ve been ordered to do.
That’s were another kind of service comes in to play. It’s called Silent Circle and it aims to secure your contacts, phone calls, text messages, and data transfers. Unlike other companies that are subject to government agencies ordering them to give up information (and prevent them from talking about it), Silent Circle is based on a peer-to-peer encryption scheme. Only the sender and the receiver can decrypt the conversation — even if a court compels Silent Circle to “listen in”, it cannot. That’s not how the system works.
Until now, however, that’s just been one component of bringing “privacy” to your smartphone, it’s expensive, and it’s been an app that you install on an otherwise insecure platform — the proverbial “chink” in the armor.
That’s where Blackphone comes in, and we got our hands on it at MWC.
What is Blackphone?
Blackphone is a smartphone built from the ground-up with security in mind. It’s operating system is based on some version of Android, but is designed with security and control first. It’s called PrivatOS.
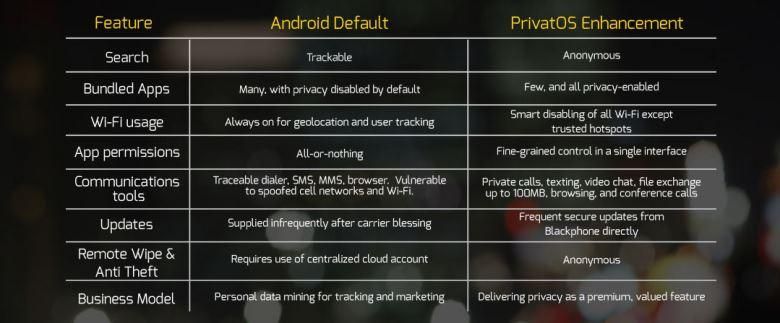
Apps with permissions that are “all or nothing” in Android are configurable with “fine-grained control in a single interface” on Blackphone. While we’re not sure exactly what that means, in general, you’ll be able to fine tune what an app can — and cannot — do.
Apps are only one thing you do with your phone. The rest of your daily tasks are addressed by other solutions built in to Blackphone.
Voice and Video
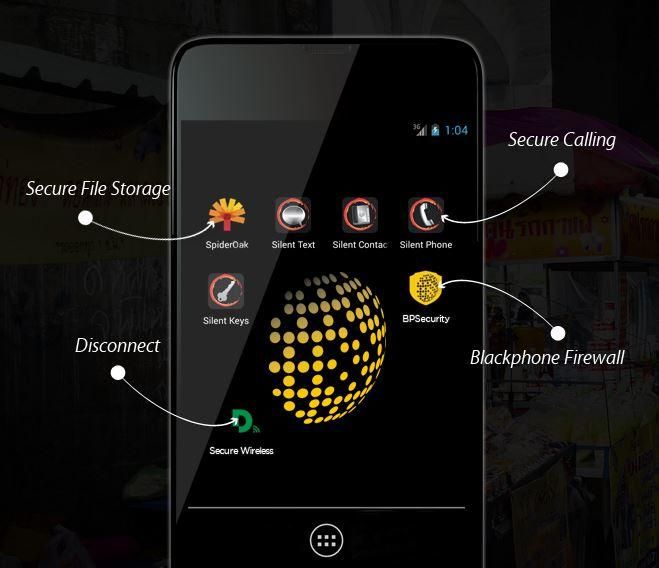
Blackphone uses the Silent Circle service to lets you make and receive secure phone and video calls (with the ability to switch between the two in-call). You can even hold a conference call with up to six Silent Circle users.
These calls are encrypted peer-to-peer, rather than at a cell tower or service provider. Everything you say leaves your Blackphone encrypted in such a manner that only the recipient can decrypt it, and vice versa.
Text Messaging
Text messaging operates much the same way that calls work. Silent Text lets you send texts and encrypted files (up to 100MB) to your recipient, as long as they are a subscriber of Silent Circle.
One problem with today’s text messages and attachments is that they can be saved and spread beyond what the sender intended. To combat this on Blackphone, the sender can enable “Burn Notification” to recall a Silent Text, so all traces of the text message and attachments are “dissolved”.
File Storage
Of course, a device is only as secure as someone’s access to that device. Though we don’t know what measures will be in place to keep unauthorized users out, the files on the phone will be stored securely.
Geo-Location
Another area of concern is geo-location: the ability to pinpoint exactly where you are on the planet. On the surface, simple GPS functionality isn’t a problem, it’s only when that information is “shared” with a 3rd party that things start to get creepy. Far too many apps and web sites do this today.
Blackphone comes with a secure geo-location feature which lets you decide when to — and when not to — include geo-location coordinates.
Web Surfing, Email, & WiFi
WiFi is a somewhat scary beast. Even if you are not connected to a given access point, your WiFi adapter is busy talking to every WAP out there. It does so with a handshake that includes your MAC address — which uniquely identifies your device, and could, by extension, uniquely identify you.
Since the location of that WAP is known, the strength of your signal is known, and WiFi can’t nominally travel more than several hundred feet, your relative position can be deduced — and reported back to whoever controls that WAP. All this without you even connecting to an access point, just by having your WiFi turned on.
Blackphone includes a utility which protects you from this snooping, and only lets you connect to trusted access point.
Web surfing, however, it somewhat problematic. Many sites require that you log into them to comment and to remember your preferences. This is made easier by teaming up with various sites like Facebook and Google, so you only have to log in to one service. That’s convenient, but not all that secure from a privacy standpoint.
Additionally, most sites on the Internet do not force SSL traffic, letting you communicate over non-encrypted HTTP instead, letting anyone along the way snoop in on your web surfing. Blackphone may address these, but nothing was mentioned of them in its literature.
Email isn’t mentioned anywhere in Blackphone’s literature, either. This is strange considering that one of the founders of the project created PGP, which is heavily used for email encryption. Why this wasn’t included is anyone’s guess.
The Achilles Heel
Last, but certainly not least, is Blackphone’s apparent Achilles Heel. The phone itself is built around secure communications. To accomplish that, you’ve got to talk with someone else on the Silent Circle network. Joining that network isn’t cheap.
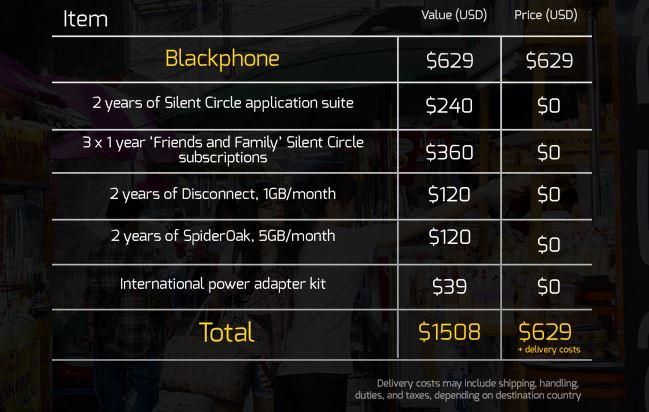
Calling, texting, and file transfers cost US$99.95 per year. If you want to be able to apply the same encryption to outgoing calls to non-Silent Circle members it will cost $249.95 more. $350 per year, per person, that’s not cheap. I’m think I may be in the wrong business! And that’s just the calling part of the package.
Blackphone includes all this, and quite a bit more, just by purchasing the phone. According to the numbers at its website, each Blackphone provides almost $880 of services when you purchase the $629 phone. It looks like that’s only 2 years of service, at which point we assume you’ll either buy a new phone and extend the serves again, or will have to pay the full price for each service a la carte going forward.
Regardless, your total protection won’t be reached until everyone in your social circles uses Blackphone’s services — which we don’t see happening any time soon, though the phone does come with three Silent Circle memberships — one for you, and two for friends or family members.
Don’t get us wrong, some protection is better than none at all. As long as you limit your communication to only those pieces that Blackphone is designed to secure, you’re very well protected. There are still a lot of holes that need to be filled, including a few fairly obvious ones that should have been taken care of prior to launch.
We’ve seen the hardware. We’ve read the literature. We have yet to go hands-on with the software, which is really what Blackphone is all about. Perhaps our concerns are unwarranted, but, for the time being you may want to hold off until we’ve got a review online before you jump right in and buy a Blackphone for yourself.