Security & Privacy are two vitally important components of any successful society. Today’s connected world, where we carry computers in our pockets and share all our details on social networks, makes them even more so. So far in this series, we’ve talked about encrypting your Internet traffic using a VPN, how to avoid getting infected by malware, how to physically secure your phone, how to encrypt your communications, and more.
—
When I worked for an advertising agency in the late 1990’s, a client of ours had developed one of the first PCMCIA-based WiFi adaptors. They didn’t call it WiFi back then, it was “wireless networking adaptor” using “802.11a” and the brand-new “802.11b” wireless networking protocols. Those weren’t very catchy names, and it was our job as an ad agency to sell them to an audience who didn’t know what they were – let alone why they “needed” them. Back then, to connect to the Internet you typically connected a phone line to a modem, dialed out, listened to a series of squeaks and squawks, and when your ISP picked up you were online – sometimes at a whopping 33.6Kbps (yes, kilobits per second). Today, my smartphone connects at around 10 megabits per second – that’s about three-hundred times faster.
Similar to your home computer (which had a port or slot you could plug a modem into), your PDA (personal digital assistant) had a slot you could plug a modem into. These modems plugged into the telephone line. ISPs had racks and racks of modems hooked up to hundreds of phone lines waiting for your computer to call. Of course you had to be close to a phone line (an actual, physical phone line) to connect, but it worked. Some cell phones had wireless internet capabilities – GPRS (not LTE, not HSPA, not even EDGE) – but most of them didn’t, which is why they needed these new “wireless network adaptors”.
With the rise of what would eventually be called “WiFi”, those ports (or slots) could be connected to a wireless modem. Unlike the modems which were commonplace back then, these wireless network adaptors required a high speed internet connection, a router, a hub or switch, and a wireless access point to be able to get your device online. These devices were typically separate pieces of hardware and required a pretty good understanding of computer networking to install and maintain. Today, all of these devices are usually combined into one unit and are relatively easy to install.
Moving from the corded modems of yesteryear and going wireless brought with it a whole bunch of freedom – but with that freedom came some pretty hefty security and privacy concerns.
Wireless Security
Security was a big concern back in the late 1990’s – so much so that they named the method for security this newfangled networking protocol “Wired Equivalent Privacy” (WEP). Yes, they actually claimed that their security protocol was every bit as “private” as if you were connected via a physical wire – despite being able to connect wirelessly from thousands of feet away.
Unfortunately, eventually in practice, WEP was anything but private. An iteration of WEP came and went, followed by newer security protocols. Today we’re “secured” by things like WPA2, PSK, AES, and TKIP. We’re not going to talk much about what these are and what they do, but each plays its part in trying to make our wireless communications “private”.
To take advantage of this “privacy” (regardless of how strong or secure it actually is), you’ve got to configure your wireless device to talk to the wireless access point using some kind of key. Short keys aren’t as secure as long ones, and long ones are hard to remember, hard to type in, and are a pain to use.
Traffic Monitoring, Packet Sniffing
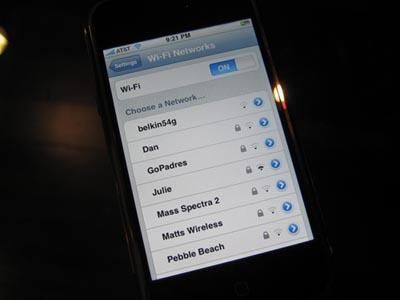
To make things easier for users, many network providers don’t secure their access points with keys – they just leave them unsecured. Doing so makes it super-easy for customers to login, but also super-easy for even casual “data voyeurs” to spy on your network traffic.
What’s “network traffic”, you ask? Think about everything you do online: sharing pictures (whether casual or intimate), sending and receiving email, posting detailed information about your daily activities, buying and selling stuff, and even banking. Without a secure connection (such as “belkin54g” in the image above), all your information is sent over an unencrypted connection from your device to the wireless access point.
Thankfully, financial institutions have been using SSL/HTTPS as their communications protocol for a very long time. This means that your information is encrypted and sent to their server regardless of what kind of network you’re on or how it’s secured. Most social media networks default their traffic to HTTPS, and there’s a push for every website and web service to use HTTPS by default. Google is even starting to penalize sites which aren’t reachable via the encrypted protocol.
Now, we even have VPNs (encrypted, virtual private networks) which serve as another layer of encrypting security (which I highly recommend using), and can help mitigate “unsecure networks” which don’t use encrypting protocols.
Spoofing
When connecting to public Wifi, a trick the bad guys sometimes employ is “spoofing” the name of what you might think is a legitimate access point, and setting up their own with a similar name.
For example, while drinking your favorite hot chocolate beverage at Starbucks you may see networks named “Starbucks”, “Starbucks Premium”, “Starbucks 5G”, or “Starbucks (High Speed)”. Which of those is the legitimate wireless network hosted by Starbucks? Even the employees may not know. One (or more) could be some guy on a laptop who is bridging the imposter WiFi network with his cellular connection (or even the legitimate Starbucks network), trying to trick you into using his network instead of the real one.
Since he’s the “man in the middle”, he can snoop on your traffic and even serve up fake versions of websites (PayPal, Amazon, your bank, social networking sites, etc.) to collect your login information so he can use for “less than honorable” purposes.
To avoid being duped by these sorts of spoofing techniques, you’ve got to know what to look for – and actually be looking for it. Neither is an easy task.
Location Tracking
The last item I’d like to address is something a bit more concerning – but something not a lot of people seem to be worried about yet: location tracking.
A local employer I am aware of utilizes a pretty sophisticated wireless access point system for their guests and employees. This system allows the company to monitor traffic and apply rules to what sites can and cannot be visited. While there’s nothing overtly wrong with that, the technology also provides a “heatmap” to “help identify areas of poor coverage”. That sounds really cool! After all, we all want a strong WiFi signal, right?
What it really does is use triangulation to map the locations of each client device within range of the access point.
Read that again.
Notice that they system isn’t locating (and plotting on a map) each client device connected to the access point, but each and every device within range of the access point.
Yes, that means a person with a phone, tablet, or even a WiFi-enabled smartwatch or even a car with a WiFi hotspot in it will show up as a device (complete with MAC address and other identifying information) on the map. An employer or retailer can know where you are, when you’re there, how much time you spent there – and if you connect to their network through a portal where you provide your name, email address, or phone number, now they can personally identify you – and wherever you are.
While that’s scary enough when applied to a school, employer, or even a shopping mall, imagine the implications when municipalities and other governmental entities offer “free WiFi” to residents, workers, and visitors. New York City and London recently rolled systems like this by converting their payphones and even light poles into “municipal WiFi hotspots” and “kiosks”.
Every person who carries a WiFi enabled device with them can be tracked. The people they’re with can be tracked. Even if you have the WiFi on your device turned off, the device will occasionally turn it back on to “look around”, and then turn itself back off again – allowing it to be seen by any wireless access points in the vicinity.
No, it’s not sci-fi. It’s a story set in some dystopian future. It’s not a conspiracy theory. It’s here and it’s now, and short of putting your device in a signal-blocking Faraday pouch, there’s nothing you can do about it.