Twitter has been all a buzz recently because Mike Davidson of Invisionapp realized that one email app called Superhuman is using an embedded image and therefore external HTTP requests to track which email recipients open which emails that you send to them. It keeps track of how many times that person opened the email too, and generates their location based on the IP address of the HTTP request. Mike Davidson’s extensive blog post about this issue is worth a read. This is only possible if your email program is set to automatically download embedded external images just like any web browser would do.
This has been normal practice among many email marketing systems for over two decades… ever since email programs gained the ability to load HTML-based email messages that linked to external images on the web. It’s how companies know their emails are working and are worth sending out because they’re getting in front of people’s eyes.
Mike Davidson blames the Superhuman app for making this technique of monitoring server logs in order to tell who viewed the email when a little too accessible to normal consumers. That’s a valid point, but what about the companies who make the email programs that receive messages? Shouldn’t they share the blame in allowing this to happen without the user’s knowledge?
10 years ago practically every email program blocked external HTTP requests (such as embedded images) by default and on purpose so that your privacy wouldn’t be violated. Can you believe that some email programs even allowed scripts to be run? That was a major privacy nightmare!
It’s all allowed by default now
Fast forward to today, and every default email program on every major platform from Apple, Google, and Microsoft has actually turned off those privacy protection options by default! They don’t even tell you about it anymore!
As soon as you open an HTML email that loads images from an external web server (all of them do), your Internet Protocol address (location), date, time, and user agent string (what type of device you’re using) gets sent to the server logs of whatever server the person who sent you that email is using. This happens in all cases. What the other end is doing with that information is unknown. In the case of the Superhuman email app, their image hosting server is associated the image(s) in the email to the unique URL used to load the image so that their server can identify which email you’re opening. Then they’re using that information to show the customer which recipients opened their email at what time (every time) and from what kind of device in whatever location. This isn’t unique to Superhuman. There are many email services and plug-ins that do this.
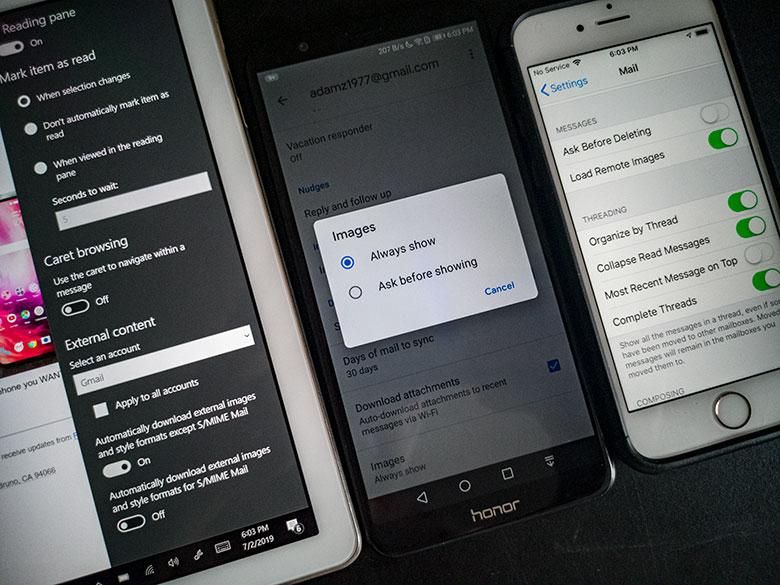
I looked at Apple Mail on iOS, Gmail on Google Android, and Mail on Windows 10… the top 3 default email apps on smartphone and computing devices these days. All of them have external image loading turned on by default. Turning off automatic external image loading is always one of the first things I do when setting up any new email program because it’s the responsible thing to do. Most other 3rd party email programs leave image loading on by default too. Even programs like the full Office Outlook which used to be very good about warning users of privacy problems have been updated to show images by default instead.
Mozilla Thunderbird is one email program that’s still very good about actually notifying its users about potential privacy issues. Thunderbird gives you some of the most extensive options for controlling remote content that I’ve seen. While most other email programs give you basic options for not loading any images, Thunderbird actually shows you each URL of where the remote content is coming from thus allowing you to choose to load specific trust-worthy sources.
Know that you’re being tracked
Luckily just about all email programs have the tools built in for you to block these tracking techniques so that you’ll only receive the actual text of the message. So you might want to dig through the settings and turn off the automatic download of external content when you open an email if you want to be more responsible about email… or at least be aware that every time you open an email with images in it, that information is getting sent to a server that has already logged the request.
By the way, if you click a link in an email (or literally anywhere), that can also be tracked in exactly the same way the loading of an image in an email (or in a web page) can be tracked and the server on the other end can/will collect your IP address, date/time clicked, and user agent string.