latest

This new Android Malware can subscribe you to services without you knowing: How does it work?
The Microsoft 365 Defender Research Team recently shared a post, explaining how a toll fraud malware can subscribe Android users to premium services, without them ever finding out and realizing it.

Dark Herring malware infected apps slip Google and infect 105 million users
Scammers uploaded more than 470 Dark Herring infected apps to Google Play Store and stole hundreds of millions of dollars. The malware affected more than 105 million people globally. Here's how it worked.

Pocketnow Daily: Apple is KILLING Face ID & The Notch?! (video)
On today's Pocketnow Daily, we talk about the possible changes coming in future iPhones, upgrades in the Nintendo Switch and more
More than 700,000 ‘bad’ apps were banned from Google Play last year, up 70 percent
Google Play Protect, machine learning techniques and an overall increased commitment to security made Android's main app store a more trusted and safer place in 2017 than ever before.

Samsung and McAfee ‘extend partnership’ to load up anti-malware software on Galaxy S8
Don't be surprised if you get a security app called McAfee VirusScan pre-installed on your Galaxy S8, and similar Samsung PC and Smart TV software.
There’s a RAT in Pokémon Go! And it’s not Rattata
Nope, not Rattata, though we are pretty much in weak territory right there. There is a jacked-up version of Pokémon Go! out there with a RAT in it.
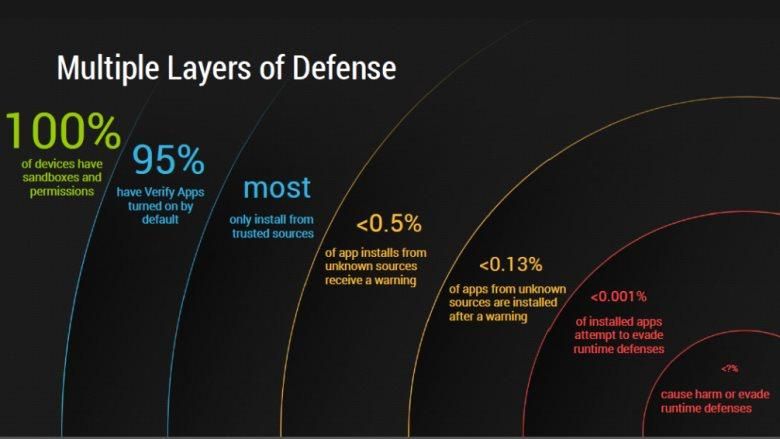
Should you use antivirus software on your Android?
Since Android is so open and lets you do pretty much anything you want with it, should you run Android antivirus software? Let's find out!

What You Need to Know About Android Trojans
Learn about Android trojans, what they are, and how to avoid them.
